Still works OK.
Sorry to bug you but can you try this??
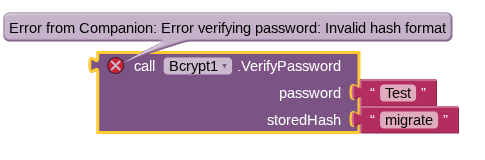
Well that obviously will not work, the string "migrate" is not a hash.
that's what i'm saying i need to migrate the passwords over from plain-text to hashes but it errors out and i need it to return false to open the more options on my wrong password menu to open the migration tool
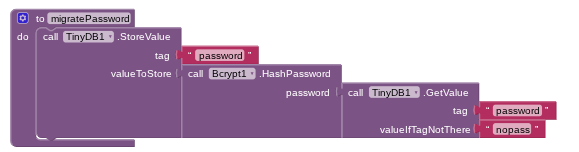
is there ANY way to detect if it is a hash?
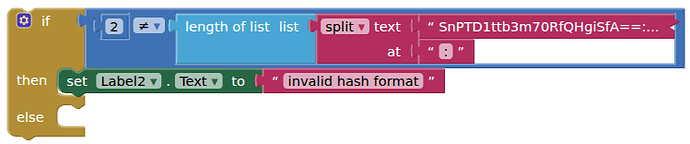
The test being used by the extension is to split the hash by :, it then checks if there are two elements in the split list. If there are not, then it generates the invalid format error. There are obviously edge cases if you provide a password string with a : in it, there are other checks if the first test passes but subsequently it cannot proceed to handle the string.
Not sure why Screen1.ErrorOccured is not catching the errors raised, need to research that, could be becuae the error is coming in from an extension, and not a built in component/method.
Ok thanks, i'll try that
It works, thank you
Hello i need to ask some questions about this extension (chatgpt):
- Documentation: Does the extension list cost factor, salt length, truncation rules?
- Rounds/work factor: Is the cost parameter configurable? Standard bcrypt uses significant work (e.g., cost 10–14).
- Salt usage: Is a random salt generated each time? Are salts long enough?
- Truncation: Does it behave like standard bcrypt (input truncated to 72 bytes)?
- Hash format: Does it return the hash in standard format with version prefix (
$2b$,$2y$, etc.)? - Verification block: Does the
CheckPasswordblock clearly accept a plaintext + stored hash and return true/false reliably? - Performance & security review: Is there commentary from users noting edge‑cases, weaknesses? In the thread you linked, one user noted “hashes will not be same as they generated last time they do randomize.”
We have not seen the extension developer here since February 2025, so you may not get an answer...
Why do you need to know all of this?
For security purposes
Really only one way to find out if your hash is secure, which is to try cracking it. Or research Bcrypt for vulnerabilities.