Pbkdf2Hash Extension Documentation
Pbkdf2Hash Class
The Pbkdf2Hash class represents an extension for PBKDF2 (Password-Based Key Derivation Function 2) hashing.
Extension .aix V4
Example .aia V4
Example .apk V4
Source.java V4
Source: Codeberg repository appsbeheerder/pbkdf2
Introduction to Password-Based Key Derivation
A Password-Based Key Derivation Function (PBKDF) is like a secret code-making machine. It's used to create strong secret codes from your password to protect your information. Reasons to use it:
-
Making Strong Codes: Passwords are usually not very strong. PBKDF makes them stronger by making it hard for anyone to guess your password.
-
Blocking Guessing Hackers: PBKDF slows down or stops people who try to guess your password by trying lots of combinations. This means it takes them a very long time to figure out your password.
-
Adding a Twist: PBKDF uses a special twist called a "salt." This twist makes sure that even if two people have the same password, their secret codes are different. This keeps your information safe.
-
Keeping Passwords Safe: When using PBKDF, a password is turned into a secret code. So, even if someone gets the secret code, they can't easily see your real password. This adds extra protection.
Think of PBKDF as a password protector.
This document provides an overview of the Pbkdf2Hash extension's functions. Their input parameters, output, and data types.
Main Functions
The following functions are used for creating and checking PBKDF2 hashes.
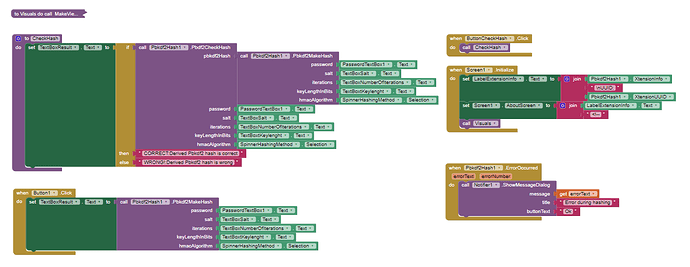
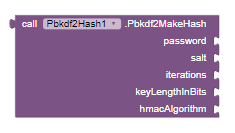
Pbkdf2MakeHash
-
Creates a PBKDF2 hash.
-
Input:
-
password(String): The password to be hashed. -
salt(String): A salt value used in the hashing process. -
iterations(Int): The number of iterations for key derivation. -
keyLengthInBits(Int): The length of the derived key in bits. -
hmacAlgorithm(String): The HMAC algorithm to use for hashing.
-
-
Output: String (PBKDF2 hash)
-
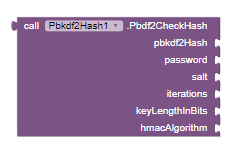
Pbdf2CheckHash
-
Checks a PBKDF2 hash against a password.
-
Input:
-
pbkdf2Hash(String): The PBKDF2 hash to be checked. -
password(String): The password to check. -
salt(String): The salt value used in the hashing process. -
iterations(Int): The number of iterations for key derivation. -
keyLengthInBits(Int): The length of the derived key in bits. -
hmacAlgorithm(String): The HMAC algorithm used for hashing.
-
-
Output: Boolean (true if the hash matches the password, false otherwise)
-
HMAC Algorithms (Helper Functions)
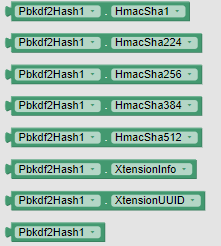
The following helper functions are used to select the HMAC (Hash-based Message Authentication Code) algorithm for hashing.
-
HmacSha1()Returns "SHA1" for HMAC hashing.
- Output: String
-
HmacSha224()Returns "SHA224" for HMAC hashing.
- Output: String
-
HmacSha256()Returns "SHA256" for HMAC hashing.
- Output: String
-
HmacSha384()Returns "SHA384" for HMAC hashing.
- Output: String
-
HmacSha512()Returns "SHA512" for HMAC hashing.
- Output: String
Helper Functions
-
IsValidHmacAlgorithm(hmacAlgorithm: String)-
Validates the HMAC algorithm to ensure it is one of the supported options (SHA1, SHA224, SHA256, SHA384, SHA512).
-
Input:
hmacAlgorithm(String) -
Output: Boolean
-
Helper Blocks
XtensionUUID()
-
Returns the extension UUID.
- Output: String
XtensionInfo()
-
Returns information about the extension, including its name, version, and copyrights.
- Output: String
Events
-
ErrorOccurred(errorText: String, errorNumber: Int)Triggered when an error occurs during extension usage.
Example app
SHA Hashing background
SHA-1, SHA-2, and SHA-3 are cryptographic hash functions, which are mathematical algorithms used to convert data into a fixed-size string of characters (a hash). These hash functions serve various purposes in computer security, such as data integrity verification and password storage.
SHA-1 (Secure Hash Algorithm 1):
SHA-1 was designed by the National Security Agency (NSA) and published by the National Institute of Standards and Technology (NIST) in 1993. It produces a 160-bit hash value.  SHA-1 is no longer considered secure for most cryptographic purposes!
SHA-1 is no longer considered secure for most cryptographic purposes!
Vulnerabilities have been found, and it is susceptible to collision attacks, where two different inputs can produce the same hash value.
SHA-2 (Secure Hash Algorithm 2):
SHA-2 is a family of hash functions that includes SHA-224, SHA-256, SHA-384, and SHA-512, which produce hash values of different lengths. SHA-2 is considered secure and widely used in various security applications, including digital signatures and SSL/TLS certificates.
SHA-3 (Secure Hash Algorithm 3):
SHA-3 is the most recent addition to the Secure Hash Algorithm family. It uses a different internal structure, which makes it distinct from SHA-1 and SHA-2. SHA-3 supports hash values of variable lengths, and it is designed to be more secure against potential future attacks.
While SHA-3 is still relatively new, it is considered a secure choice for cryptographic applications.
In summary, SHA-1 is deprecated and should be avoided in favor of SHA-2 or SHA-3 for security-critical applications. SHA-2 is currently widely adopted and secure for most purposes (SHA384 and higher), while SHA-3 offers a different design approach and is also considered secure.
This extension offers SHA1 and SHA2 hashing algorithms.
This documentation provides a comprehensive overview of the functions, input parameters, output, and data types for the Pbkdf2Hash extension.
-
©Eric M. Kok (appsbeheerder)
-
License: LGPL3 - GNU Lesser General Public License version 3
-
You are allowed to use the Pbkdf2Hash .aix (jar) extension, as part of an MIT Appathon app. https://appathon.appinventor.mit.edu/

-
You are allowed to use the .aix (jar) extension Pbkdf2Hash, as part of an MIT Appathon app. https://appathon.appinventor.mit.edu/


Extension UUID:
8764a0b8-8515-4fc4-99be-f4759b61d409