introduction
Introducing the Advanced Data Encryption Extension for MIT App Inventor, created by Mr_Kodr. This extension provides a comprehensive set of tools for encrypting and securing sensitive information, including advanced algorithms like AES, RSA, DES, and base-64. It enables users to encrypt files, folders, and entire hard drives with ease, while also providing a user-friendly interface and options for creating backups of encrypted data. The extension ensures that sensitive data can only be accessed by authorized individuals and provides an added layer of security against cyber threats. With the Advanced Data Encryption Extension,
users can confidently protect their important data with a high layer of security
blocks
Explenation
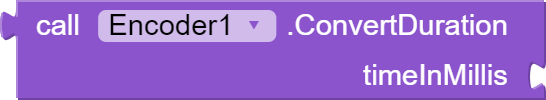
This block "ConvertDuration" takes an argument "timeInMillis" which is the time in milliseconds and converts it to a duration format "hh:mm:ss". It calculates the total number of seconds, hours, minutes and seconds and returns a string in the format "hh:mm:ss". This can be used to format the duration of media files or other time-related data.
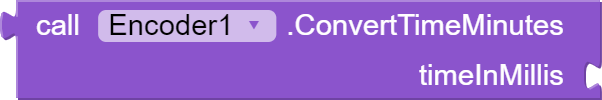
This block "ConvertTimeMinutes" also takes an argument "timeInMillis" which is the time in milliseconds and converts it to a duration format "mm:ss". It calculates the total number of minutes and seconds and returns a string in the format "mm:ss". This can be used to format the duration of media files or other time-related data.
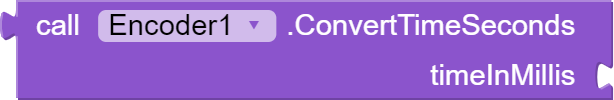
This block "ConvertTimeSeconds" also takes an argument "timeInMillis" which is the time in milliseconds and converts it to a duration format "ss". It calculates the total number of seconds and returns a string in the format "ss". This can be used to format the duration of media files or other time-related data.
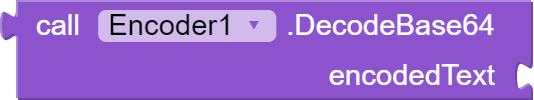
This block "DecodeBase64" takes a single argument, "encodedText" which is a string representing the encoded text that you want to decode. This function uses the built-in Base64 decoder from the Java standard library to decode the encoded text. The decoder takes the encoded text as an input and returns an array of bytes. The returned byte array is then converted to a string using the new String() constructor and this decoded string is returned as the output of the function. This block can be used to decode any text encoded using the base64 algorithm and can be useful for decoding data that has been encrypted or for decoding encoded data used for authentication.
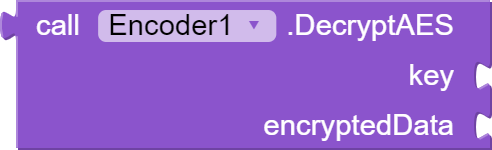
This block "DecryptAES" also takes two arguments, a key and the encrypted data, and decrypts the data using the AES algorithm. The key must be the same key used to encrypt the data. The function uses the key to create a SecretKeySpec object, which is used to initialize the AES cipher. The cipher is then used to decrypt the data and the original data is returned as a string.
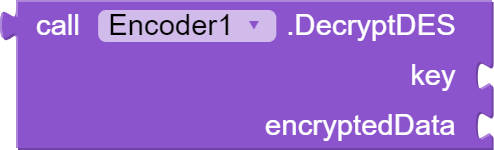
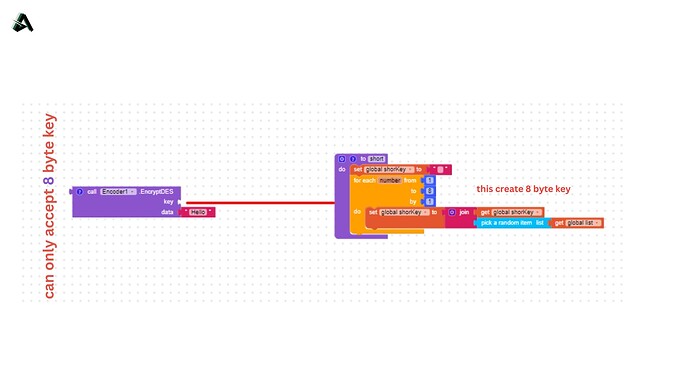
This block "DecryptDES" also takes two arguments, "key" and "encryptedData". The key must be 8 bytes long, and the encryptedData is the message that needs to be decrypted. The function uses the Data Encryption Standard (DES) algorithm to decrypt the data. The decryption is performed using a SecretKeySpec object, which is initialized with the key bytes and the "DES" algorithm. The Cipher object is then initialized with the decryption mode and the secret key, and the data is decrypted using the "doFinal" method. The decrypted data is returned as a string.
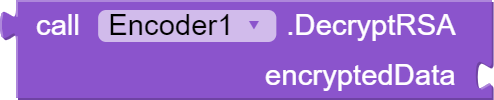
[the most secure between them] This block "DecryptRSA" takes a string argument "encryptedData" which is a base64 encoded string, that was encrypted using the RSA algorithm. The function creates a Cipher object using the RSA algorithm and initializes it with the private key in decryption mode. The encrypted data is then decoded from the base64 string and passed to the doFinal method to decrypt it. The original data is then returned as a string.
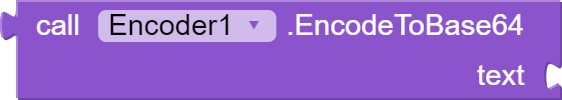
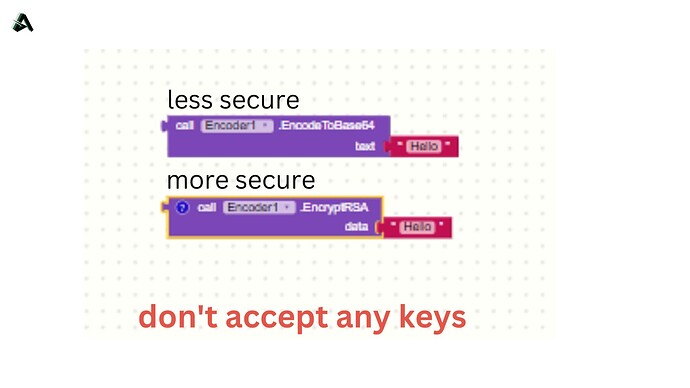
This block "EncodeToBase64" takes an argument "text" which is the plain text to be encoded and returns the base64 encoded string of the text. Base64 encoding is a process of converting binary data to a ASCII text format. It is commonly used to transmit binary data over a network connection or to store binary data in a text file.
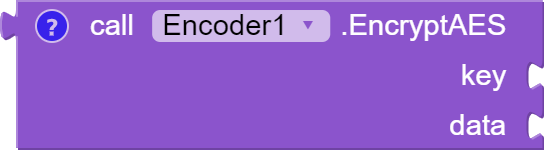
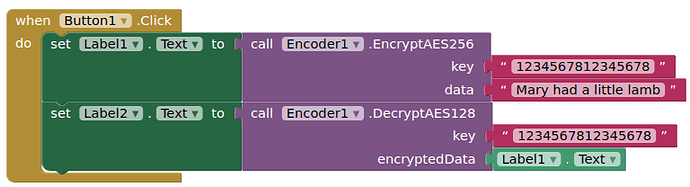
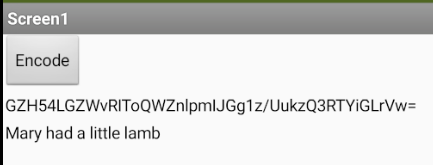
The function "EncryptAES" takes two arguments, a "key" and a "data" , and encrypts the data using AES encryption algorithm. The key must be a multiple of 8 bytes long could be 16,24, or 32 bytes long. The function uses the key to create a SecretKeySpec object, which is used to initialize the AES cipher. The cipher is then used to encrypt the data and the encrypted data is returned in Base64 encoded format.
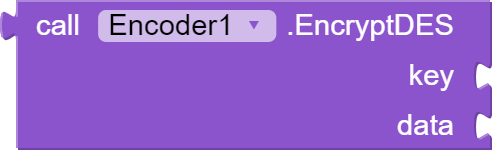
This block "EncryptDES" takes two arguments, "key" and "data". The key must be 8 bytes long, and the data is the message that needs to be encrypted. The function uses the Data Encryption Standard (DES) algorithm to encrypt the data. The encryption is performed using a SecretKeySpec object, which is initialized with the key bytes and the "DES" algorithm. The Cipher object is then initialized with the encryption mode and the secret key, and the data is encrypted using the "doFinal" method. The encrypted data is then encoded to base64 and returned as a string.
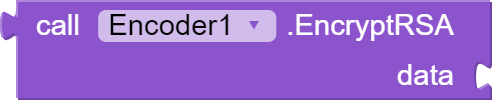
[the most secure between them] This block "EncryptRSA" takes a string argument "data" and encrypts it using the RSA algorithm. The RSA algorithm is a public-key encryption algorithm that is widely used to secure sensitive information. The function generates a new key pair using the KeyPairGenerator class and initializes it with a key size of 2048 bits. The public and private keys are then extracted from the key pair and stored in the respective variables. The function then creates a Cipher object using the RSA algorithm and initializes it with the public key in encryption mode. The data is then encrypted using the doFinal method and the encrypted data is encoded to a base64 string and returned.
Tutorial
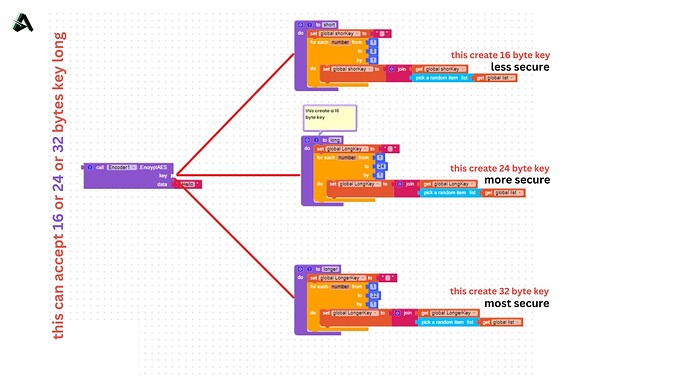
The conditions for the key for the AES-128, AES-192 and AES-256 functions is that the key must be multiple of 8 bytes long for example each one of them can accept 16 or 24 or 32 bytes long key.
The difference between using AES with a key length of 16 bytes, 24 bytes, and 32 bytes is the level of security provided. AES-128, which uses a 128-bit key and input 16-bytes of long key, is considered to provide a good level of security for most uses. AES-192, which uses a 192-bit key and input 24-bytes of long key, provides a higher level of security and is typically used in government and military applications. AES-256, which uses a 256-bit key and input 32-bytes of long key, provides the highest level of security and is typically used in highly sensitive applications such as financial transactions and classified communications.
For the DES function, the key must be 8 bytes long only.
For the RSA block, no key length specified, but it is commonly used with a 2048-bit key.
The base64 function does not have any specific key requirements. It is a method for encoding binary data as ASCII text. The functions that use base64 are primarily used to encode or decode data as a string, rather than encrypting or decrypting it.
Our socials
Download
Aix
❒ com.mrkoder.Encryption.lol.dev.aix


 Don't guarantee something that your extension cannot do.
Don't guarantee something that your extension cannot do.