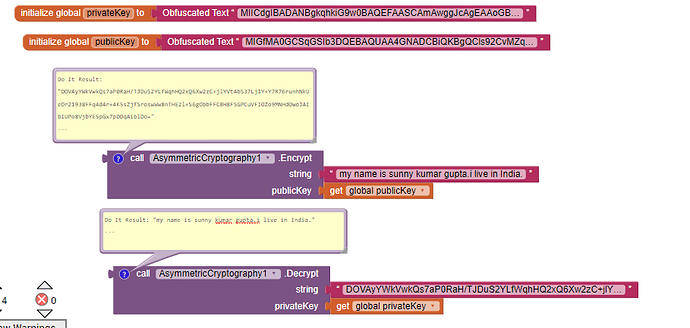
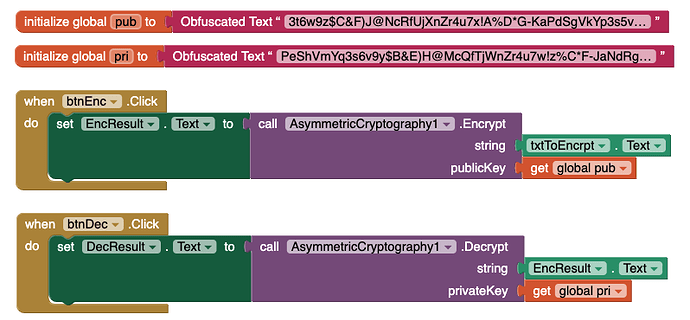
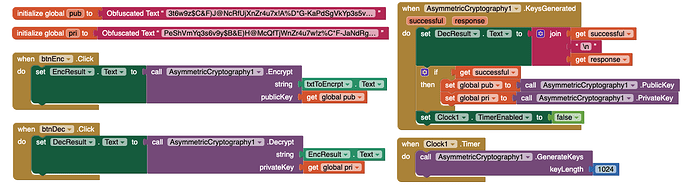
After a bit more testing i got the obfuscated text one to work. Copying the 848 characters dropped one off somehow. So we have to run generateKeys even if we already have the keys…?
Here also an html page using javascript and the jsencrypt library which can decrypt strings generated in the app. (You will have to fiddle about a bit, but you should see how it works).
Always good to have a back door !
encrypt.txt (2.7 KB)
I am not sure but this is probably because of using special characters.
No ![]()
I have already fixed that in v 2
I have no idea that why it is not working for you (maybe you are using v1).Here are my test results:
As I mentioned, for some reason copying the key to the obfuscated text block somehow dropped off one character. I sorted that and it worked fine. I will find your version 2 and try that out.
V2 works fine without key generation. Thank you.
Now it is just a matter of getting the private key to others!
Welcome Sir ![]()
Either you have to exchange keys via database or use built-in keys i.e. stored in obfuscated text.
You never share the private key. That's why it is private. You share the public key and people use the public key to encrypt data. The private key is used to decrypt the encrypted message. Although in most implementations what actually happens is you generate a symmetric key, use the symmetric key to encrypt the message, and then encrypt the symmetric key with the public key. Symmetric encryption is usually faster than asymmetric encryption and sometimes even supported in hardware.
No way of any user decrypting anything in that case....
That’s not true. An example flow for two users to exchange messages would go something like this:
- User A generates a keypair and publishes the public key via CloudDB
- User B generates a keypair and publishes the public key via CloudDB
- User A retrieves the public key of User B and uses it to encrypt a message
- User A publishes the encrypted message via CloudDB
- User B receives the message, such as through the DataChanged event, and decrypts the message using their private key.
Neither user reveals their private key in this scenario. The public keys are all that are necessary to establish the secure channel. For example, my PGP public key (which you could use to send me encrypted messages), is available here. The private key only ever lives on my machine (plus backup disks), and has a passphrase so that even if someone got a hold of the keychain they would need to know the passphrase in order to decrypt the messages (or brute force the private key, which is theoretically possible but practically infeasible as far as we know).
Note that my scenario above doesn’t cover signing the message. For example, another User E might want to pretend to be User A and send User B a message encrypted using User B’s public key. Usually to counter this, User A includes a digital signature signed with User A’s private key, which can be verified using User A’s public key. This way, User B can confirm that User A was the original sender. Since User E doesn’t have user A’s private key, they can’t forge a message signed using that key. If you were to reveal the private key, you would have no way of knowing if someone is reading your messages or masquerading as you.
This exchange is essentially how SSL works. The server has a private key and its public key is included in the certificate sent to your browser. Your browser creates a temporary key pair and exchanges the public key with the server. The browser and server then negotiate a symmetric key pair over this asymmetrically-secured connection (see my previous note about speed), usually using Diffie-Hellman. If the server’s private key is ever revealed, an adversary could decrypt the exchange of symmetric keys and then decrypt all communications to that server, which would reveal passwords, banking information, etc.
I know what you are saying and how it works, just looking at the practicalities/options of using this thing in an app, with PRESET public and private keys. If users only have to decrypt data provided from outside the app, or stored in the app to be distributed, they will need the private key, using this extension, with the private key stored, obfuscated, in the app that is distributed to users.
Finally someone who could explain this to me ![]() Also thank you for sharing my security concerns, @ewpatton
Also thank you for sharing my security concerns, @ewpatton
I always get this error in Android 10
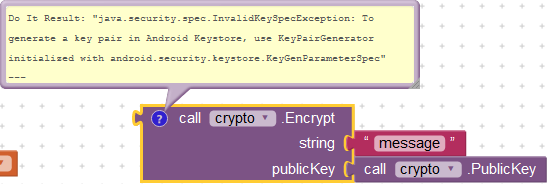
I think key pair is not generated.
Try generating key pair or using external key pair.
Yes, you’re right. It works now 
Hi @vknow360,
I downloaded your V2 from the link above and followed as what you’d shown above but It seems it still need to be initialised.
First error is Parsing then when the button pressed again it, it is the initialisation. Is there any missing parts? I made it worked when you have to place and initialisation same as with @TIMAI2, attached is the aia. Thanks for your help and patience. V2EncDec_copy.aia (9.5 KB)
wow is this you made it yourself
@vknow360,
This is the V1 that really worked for me, it took me a while to finally made it work, the only solution is to use a Clock and not the Screen.Initialize, again thanks for your help.
Hi @Ragna
I am sorry for not replying.(for a month)
I was unable to check it due to lack of time.
But now I am free so I can check.
Give me some time.